The Data Blog |
|
Cyber Security Consulting companies are always interested in new value-added advice they can provide to their clients. One potentially lucrative area is recommending a synthetic data solution that would eliminate the risk of a data breach through your development, laboratory, and testing ecosystems where most breaches occur.
This is potentially a very lucrative market opportunity for these consulting companies. Software development globally is estimated to be around $500B annually, of which about 30% or $150B is for test data provisioning. This is all being done today through a process that modifies production data with the potential to convert to services revenue through a new disruptive synthetic data process. ROI’s are strong for the end customer eliminating repetitive labor tasks, compressing development times and removing a security risk area, which drives high margins for these new professional services. Learn more at www.exactdata.net
4 Comments
As of today, most companies in the world still use big data with big costs to account for all of their testing and production value. Companies like Amazon and Oracle rely on large datasets which while are sufficient, aren't able to be used as much after a few years due to changing standards in the world.
By utilizing artificially generated data, these companies would be able to mold their data so it can be adaptable with the next big trend. Thus, be applicable in years to come rather than have to continually spend a lot on R&D and production testing operations to yield very similar results to its synthetic data alternative. Financial analytics, artificial intelligence, and machine learning are just a few of the benefits you may reap from switching over to a synthetic data alternative, and with the technological advances being made in our society, getting ahead of the curve is the key to being the next big thing in the industry. When expanding out and scaling a company, expenses don't have to expand with you; minimizing costs on data and production testing is possible in several ways, but none better than making that switch to synthetic data. Each type of database and database management system has its associated advantages and disadvantages, but when should you use one over the other? Is there a certain situation that one of these will be much more beneficial than another, or is the reverse true where using one will make it even harder for you to store and retrieve data?
Database management systems alike allow user access and data manipulation within a database but the way users actually interact with each database differs per usage of the DMS. For example, in a relational database management system typically users will use SQL for data manipulation and the process is inherently easy, making RDBMS' historically very popular. However, relational database management systems are not without their limits; it is hard to scale relational databases horizontally, or adding more to machines to your resources to allow for faster processing. As such, you may want to look into a different type of database management system if your work will involve horizontal scaling opposed to vertical scaling, the upgrading of system hardware. So what other types of database management systems can one use? NoSQL databases such as graph databases and key-value store databases use document store objects to match a certain key to its one to one value such as integers, strings, and JSON objects. As opposed to relational databases, NoSQL databases tend to be highly scalable while also being quite efficient. Typically they are used for session management, account creation and set-up, and message-queuing. NoSQL databases are not without their disadvantages however; their 'eventual consistency' as part as their BASE structure as opposed to ACID results in some periods of time without updates rather than on the fly updates every time a change is made. Additionally, there isn't much of a standard in terms of uniformity for many NoSQL databases yet. Network database management systems, invented by Charles Bachman, use network structures to define relationships between different entities, typically on larger networks of hardware. In network database management systems, parent nodes can relate to "member" or children nodes through many-to-many relationships. Thus, each node can connect with another making the database structurally simple and easy to follow. Consequently, this structure is difficult to change because of how connected each node is to one another and therefore one change can affect the whole database. Network database models are most commonly used when one needs a flexible way to represent entity relationships but not necessarily modify them. There are many other types of database management systems one can use to interact with their database, and each have distinct advantages and disadvantages, Thus, it's always important to carefully examine your database, your goals for it, and how you'd like to interact with it to establish which database management system is right for you. When one thinks of cyber security, cyber attacks and hackers, one doesn't typically associate the manner with terrorism. However, cyberterrorism and foreign intelligence cyber attacks are becoming more of an issue as the internet evolves into a more mainstream medium around the world. Just this past July, hackers from Russia have been accused of electronically meddling in international affairs and general elections of the United Kingdom and of trying to steal information relating to a potential COVID-19 vaccine. Likewise, The United States has reportedly launched cyber operations against countries such as Iran, China, Russia, and North Korea via the CIA to 'cause disruption and leak information to the public.'
Cyber attacks can take many different forms; phishing emails, keystroke monitoring, malware downloads, and web activity monitoring, which makes tracing them hard to begin with. Additionally, attacks can be historically hard to trace due to the sophisticated nature the operations tend to take. Why, anyone can download a VPN to fool online tools and fool browsers and companies by placing their signal in another country; if just about any computer user can change their location on the internet, just imagine what the most advanced hackers are capable of. Fortunately, there are several ways to combat cyberterrorism which range from flooding the internet with fake data to discredit the findings of any successful cyber operations to full fledged task forces and commands to fight it such as the United States Cyber Command or China's Blue Army. For more information about how the United States combats cyberterrorism, visit the United States Cyber Command website. One newly emerging but very important aspect within the financial and banking industry is the element of cryptocurrencies like BitCoin which are constantly fluctuating in market value. While some praise cryptocurrencies for being more secure and manageable compared to regular currencies, skeptics criticize it for being less traceable, less stable, and more susceptible to being stolen through hacks and cyber attacks. In 2019 alone, more than $4 billion worth of cryptocurrencies had been stolen, so if banks and other financial institutions were to start using cryptocurrencies at a higher level, they would need to invest in their own defense and cybersecurity activities first.
This means mobile and web portal security would both have to be upgraded tremendously to remain as safe as possible. Online banking already poses a big threat to security due to the risk of potential cyber attacks, but with cryptocurrencies coming into play, web and mobile portals will have to be monitored more closely than ever. So the ultimatum is, should banks and financial institutions begin carrying cryptocurrencies if their consumer groups have a demand for it? Would that ruin the point of or demonetize cryptocurrencies? Only time will tell, but as these financial technologies become more advanced so will those who will attempt to hack them. With the recent Twitter account hacks of notable celebrities and politicians such as Barack Obama, Bill Gates, and Kanye West, the question of "can you ever be too secure?" comes to light. Notable people with millions of followers on Twitter were being hacked, so why can't it happen to you? Even if your accounts aren't the ones being directly hacked, what if you're a victim of an indirect hacking? Many Twitter users were tricked into sending over bitcoin to the person behind these celebrity account hacks, so despite not even being touched, their information and assets were rendered vulnerable.
While the cyber security industry is certainly seeing improvements over time, computer hackers are also becoming more advanced in how they can steal information or assets from the general public. They've evolved from spam emails and phone calls, which many people still fall for, to password cracking, IP tracing, and webcam spying over the years and soon may hit the next big thing as well. So how do you keep your information secure? Here are a few quick tips you can try! 1) Make sure your password is different for every website/account you have 2) Keep your virus protector and anti-malware subscriptions up-to-date 3) Don't click any links on social media, emails, or other websites that you don't recognize 4) Don't connect to public WiFi when you have sensitive information that can be easily accessed 5) Remember you aren't above cyber security; just because it hasn't happened to you yet, doesn't mean it won't. Anomaly Detection, a common topic in machine learning, is a field dedicated to detecting unexpected or behavior-deviating trends and events in data sets, which if left unnoticed, can disrupt or skew the data as a whole. Typically used in heavy data domains such as finance, economics, statistics, and other technology sectors, anomaly detection is becoming more popular in the world to ensure the absolute perfection of data findings. While once not relied on due to the criticisms anomaly detection algorithms grew for having high false-positive rates, algorithms over the years have developed significantly and the field is becoming more popular than ever.
Software engineers, data analysts, and statisticians, are several among many of the professions who in the future will rely on anomaly detection to ensure their findings are as accurate as possible. Using more advanced techniques such as multivariate anomaly detection, findings become even more reliable as outliers are signaled out in an even greater pace. For example, anomalies can be spotted in VIF tests to search for multicolinearity, ensuring that the data isn't skewed because many factors have the same backbone to rely on. On the other hand, logistic regressions can show exactly where outliers lie in comparison to the two variables they're tested against to ensure outliers that have nothing to do with our data are left out as well. Anomaly detection is becoming more prominent in society and as such, machine learning algorithms and all of technology continue to advance each and every year for the benefit of data scientists everywhere. ExactData and Edgeworx Excited to form Partnership
ExactData and Edgeworx will work closely together to market and distribute synthetic data to Canadian technology sectors ExactData and Edgeworx have formed a partnership to market ExactData’s synthetic data to relevant businesses across borders that would benefit from the innovative technology. Not only will this help expand the opportunities and growth for artificially generated data, but it will open the world of possibilities for model testing and training using synthetic data as opposed to its traditional authentic counterpart. Synthetic data generation is predominantly used in place of authentic data due to its more flexible and adaptable nature. As it can be continuously generated for several different purposes, synthetic data has the potential to test much more scenarios and train advanced applications in a shorter period. Common use cases for synthetic data are applying it for machine learning, threat detection, and AI behavior modeling, all of which are fields that have benefited greatly from the use of synthetic data. Furthermore, there are many more sectors of the technology and cybersecurity industries that will benefit greatly by using ExactData’s smart data for all their data needs. Edgeworx Solutions provides clientele with all their technology needs which ranges across different fields throughout the world of modern technology. Examples include cloud networking, cybersecurity, performance optimization, data analytics, and now, all synthetic data needs. Entering new technology markets with Edgeworx help is a clear, exciting step in the right direction. Edgeworx direction and network and ExactData’s technology will make a great team for years to come that shows both promise and endless possibilities. Edgeworx website can be found here! 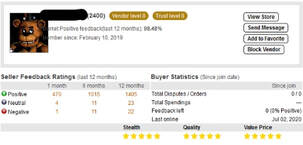 Every company or government agency has had some sort of data breach at some point in time. They might not even know that the breach has happened. An interesting new strategy gaining interest within the cyber security community is the use of offensive misinformation campaigns. Misinformation campaigns involve generating synthetic databases that would be indistinguishable from the production databases and having them passed to adversaries either through a honeypot deception solution or directly placed on dark websites dealing with selling stolen data. The result is that the adversaries will uselessly expend resources trying to sort out what is real and not, place doubt on any real information they might already have, and run illicit fraud campaigns against people who do not exist. For example, the Boeing aircraft manufacturing company would leak synthetic highly confidential wing design databases that would be indistinguishable from the real ones without extensive analysis or access to other information for verification. Other examples would be Equifax leaking bogus credit reports or VISA fake personnel financial information. The confusion and harmful effects on the adversarial community is tremendous. ExactData would recommend implementing an offensive misinformation campaigns working with a threat intelligence company that has a deep understanding of the Dark Web. The TOR Network is an anonymous internet protocol which allows users to conceal their identity when browsing the internet and allows users to access the Dark Web. The Dark Web contains some of the most illicit marketplaces, advanced hacking groups, and a common method to leak sensitive information anonymously such as SSN’s, trade secrets, and military/government documents. As all the users within using TOR are anonymous. It is not possible to know if the person or website you are interacting with is trustworthy. Trust is instead developed through the interactions with the community such as product and vendor feedback for listings on the popular illegal marketplace “Empire” or dark web community forums such as “Dread”. The threat intelligence company will be able to access this community and leak the realistic synthetic data into this illegal marketplace in a credible fashion through deception techniques. The realistic synthetic data not only aids in building the trust of the adversary for direct counter measures, but also once the synthetic data is transferred into the community the desired confusion and harmful effects. Learn more at www.exactdata.net We at ExactData wish you the best for any upcoming Fourth of July celebrations, as well as any recent or upcoming celebrations for Canada Day! For fireworks lovers, we have a bit of information that may interest you! The creation of fireworks is evolving so that they can be modeled and engineered synthetically; using previous data and predictive analytics based on how well other products work, new fireworks can be created and tested virtually. Talk about a could be boom in the industry!
|
Archives
August 2023
Categories
All
Data Blog |

 RSS Feed
RSS Feed