The Data Blog |
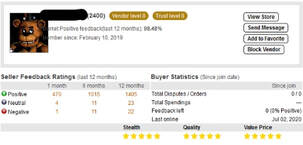 Every company or government agency has had some sort of data breach at some point in time. They might not even know that the breach has happened. An interesting new strategy gaining interest within the cyber security community is the use of offensive misinformation campaigns. Misinformation campaigns involve generating synthetic databases that would be indistinguishable from the production databases and having them passed to adversaries either through a honeypot deception solution or directly placed on dark websites dealing with selling stolen data. The result is that the adversaries will uselessly expend resources trying to sort out what is real and not, place doubt on any real information they might already have, and run illicit fraud campaigns against people who do not exist. For example, the Boeing aircraft manufacturing company would leak synthetic highly confidential wing design databases that would be indistinguishable from the real ones without extensive analysis or access to other information for verification. Other examples would be Equifax leaking bogus credit reports or VISA fake personnel financial information. The confusion and harmful effects on the adversarial community is tremendous. ExactData would recommend implementing an offensive misinformation campaigns working with a threat intelligence company that has a deep understanding of the Dark Web. The TOR Network is an anonymous internet protocol which allows users to conceal their identity when browsing the internet and allows users to access the Dark Web. The Dark Web contains some of the most illicit marketplaces, advanced hacking groups, and a common method to leak sensitive information anonymously such as SSN’s, trade secrets, and military/government documents. As all the users within using TOR are anonymous. It is not possible to know if the person or website you are interacting with is trustworthy. Trust is instead developed through the interactions with the community such as product and vendor feedback for listings on the popular illegal marketplace “Empire” or dark web community forums such as “Dread”. The threat intelligence company will be able to access this community and leak the realistic synthetic data into this illegal marketplace in a credible fashion through deception techniques. The realistic synthetic data not only aids in building the trust of the adversary for direct counter measures, but also once the synthetic data is transferred into the community the desired confusion and harmful effects. Learn more at www.exactdata.net
0 Comments
Leave a Reply. |
Archives
August 2023
Categories
All
Data Blog |

 RSS Feed
RSS Feed